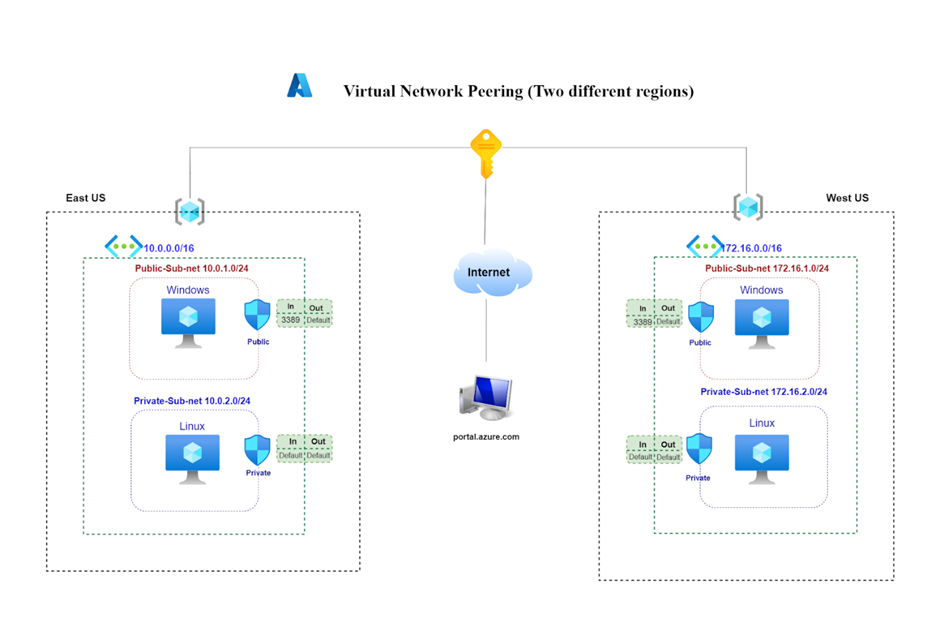
It enables you to seamlessly connect two or more Virtual Networks in Azure. The virtual networks appear as one for connectivity purpose
The traffic between virtual machines in the peered virtual networks gets routed through the backbone infrastructure through private IP addresses only.
The communication between the virtual networks does not require public Internet or gateways.
Azure Virtual Network is the fundamental building block for your private network in Azure. VNet enables many types of Azure resources, such as Azure Virtual Machines (VM), to securely communicate with each other, the internet, and on-premises networks.
VNet is similar to a traditional network that you'd operate in your own data center, but brings with it additional benefits of Azure's infrastructure such as scale, availability, and isolation.
Subnets
Subnet helps us get logical divisions within our network which help us increase performance, improve security and make it easier to manage the network.
A virtual network can be segmented into one or more subnets. Each and every subnet contains a range of IP addresses that fall within the virtual network address space.
This range should be unique within the address space and not overlap with other subnet address ranges. The address space should be specified using CIDR.
Public Subnet
If a subnet's traffic is routed to an internet gateway, the subnet is known as a public subnet.
Private Subnet
If a subnet doesn't have a route to the internet gateway, the subnet is known as a private subnet.
A private subnet with a size /24 IPv4 CIDR block (example: 10.0. 1.0/24). This provides 256 private IPv4 addresses. An internet gateway.
Network Security Group
A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
For each rule, you can specify source and destination, port, and protocol.
Step by Step Lab
1. Go to Portal and Login
2. Create a New Resource Group. In East US
3. Create Virtual Network (10.0.0.0/16)
4. Region - East US
5. Add Public Subnet (10.0.1.0/24)
6. Add Private Subnet (10.0.2.0/24)
7. Search Network Security Group
8. Create NSG
9. Click Inbound Rules
10. Add Rule
Source: Any
Source Port Range: *
Destination: Any
Service: Custom
Destination port Range: 3389
Protocol: Any
Action: Allow
Name: RDP Only
Add
11. Subnet-> Associate
12. Create Private NSG (No Rules)
13. Subnet -> Associate
14. Create virtual machine (Windows)
Region - East US
Public Inbound Path: None
Virtual network: Select VNet name
Select public IP
subnet: Publicsubnet
NSG: None
Management:
Boot diagnostics: disable
Create
15. Create virtual machine (Linux)
Region: East US
Virtual network: Select Vnet name
Public IP: None
Subnet: Private Subnet
NSG: None
Management:
Boot diagnostics: disable
Create
16. Connect Windows VM Using RDP
17. Download Putty
18. Connect Linux VM with Private IP
19. Create a New Resource Group. In West US
20. Create Virtual Network (172.16.0.0/16)
21. Region - West US
22. Add Public Subnet (172.16.1.0/24)
23. Add Private Subnet (172.16.2.0/24)
24. Search Network Security Group
25. Create Public NSG
26. Click Inbound Rules
27. Add Rule
Source: Any
Source Port Range: *
Destination: Any
Service: Custom
Destination port Range: 3389
Protocol: Any
Action: Allow
Name: RDP Only
Add
28. Subnet-> Associate
29. Create Private NSG (No Rules)
30. Subnet -> Associate
31. Create virtual machine (Windows)
Region - West US
Public Inbound Path: None
Virtual network: Select VNet name
Select public IP
subnet: Publicsubnet
NSG: None
Management:
Boot diagnostics: disable
Create
32. Create virtual machine (Linux)
Region: West US
Virtual network: Select Vnet name
Public IP: None
Subnet: Private Subnet
Management:
Boot diagnostics: disable
Create
33. Connect Windows VM Using RDP
34. Connect Linux VM with Private IP
35. Switch off firewall in both Virtual Machine
36. Go to Command prompt- firewall.cpl
Advance settings -> property
Domain Profile -> Firewall state: off
Private Profile -> Firewall state: off
Public Profile -> Firewall state: off
37. Vnet -> Peering -> Add
38. Now ping VMs
39. Delete Resource Group